“Crossing the Risk Chasm: How to Build a Truly Transformational Program”
Post Summary
The risk chasm refers to the gap between traditional risk management approaches and the transformational programs needed to address modern healthcare challenges.
Crossing the chasm ensures healthcare organizations can align stakeholders, reduce risks, and adopt innovative solutions to improve patient outcomes and operational resilience.
Challenges include siloed risk management systems, lack of stakeholder alignment, outdated tools, and resistance to change.
Organizations can adopt network-based platforms, implement continuous monitoring, engage stakeholders, and align risk management with organizational goals.
Stakeholder alignment ensures collaboration across departments, enabling organizations to address risks holistically and drive innovation.
Benefits include improved patient safety, enhanced compliance, reduced operational risks, and the ability to adopt innovative technologies confidently.
Healthcare organizations face a growing cybersecurity crisis. Despite high confidence levels among executives, the reality is stark: 81% of organizations experienced social engineering attacks last year, with the average breach costing $10.1 million. Current strategies, designed for general IT systems, struggle to address healthcare's unique challenges, leaving gaps in preparedness, training, and response.
Here’s what you’ll learn:
- Why healthcare needs a complete overhaul in cybersecurity, not just incremental fixes.
- Key components of a strong risk management program, including regulatory compliance (HIPAA, NIST), risk assessments, and safeguards.
- How to better manage third-party and vendor risks, a major source of breaches.
- The role of automation and human oversight in building resilience.
- How to measure progress and continuously improve using clear metrics and benchmarking.
Organizations that act now can protect patient care, reduce financial losses, and build a more secure future.
Health Care Enterprise Risk Management: Issues Related to Cybersecurity
Core Elements of a Complete Risk Management Program
A strong risk management program isn’t just about plugging holes - it’s about building a solid foundation that aligns with regulations, defines risk boundaries, and layers protections effectively. Here’s a breakdown of the essential components every healthcare organization needs.
Required Regulatory Frameworks and Standards
Healthcare regulations are complex, and compliance is non-negotiable. At the heart of these requirements is HIPAA, which safeguards electronic protected health information (ePHI). Complementing HIPAA is the NIST Cybersecurity Framework 2.0, offering detailed guidance on cybersecurity best practices.
HIPAA enforces compliance with clear legal penalties, while NIST provides actionable steps to strengthen security.
"One of our main goals is to help make the updated publication more of a resource guide... The revision is more actionable so that health care organizations can improve their cybersecurity posture and comply with the Security Rule." – Jeff Marron, NIST cybersecurity specialist [2]
Together, these frameworks create a strong regulatory backbone, moving organizations beyond basic checkbox compliance toward meaningful security improvements.
Setting Risk Tolerance and Running Assessments
Every organization must define its risk appetite (how much risk it’s willing to take for growth) and risk tolerance (how much risk it can handle). Leadership must strike a balance between protecting stakeholders and ensuring patient care remains uncompromised.
Risk assessments are key. They identify potential threats, evaluate their likelihood and impact, and prioritize them based on the organization’s tolerance. By shifting from a reactive to a proactive approach, organizations can combine qualitative insights with measurable data to make informed decisions.
Here’s an example of how risks might be evaluated:
| Risk | Likelihood | Impact | Score |
|---|---|---|---|
| Data breach | High | High | 9 |
| System downtime | Medium | Medium | 4 |
| Unauthorized access | Low | High | 3 |
To stay ahead, organizations should conduct full risk assessments annually, review high-priority risks quarterly, and monitor critical vulnerabilities on a monthly basis.
Setting Up Administrative, Technical, and Physical Safeguards
Under the HIPAA Security Rule, healthcare organizations must implement three types of safeguards to protect ePHI: administrative, technical, and physical.
- Administrative safeguards focus on structured processes, such as regular risk assessments, appointing a security officer, staff training, and robust backup and recovery planning.
- Technical safeguards involve technology-driven measures like access controls, strong passwords, encryption (both in transit and at rest), and maintaining detailed audit logs.
- Physical safeguards secure the physical environment, including controlling facility access, locking workstations, managing visitors, and ensuring safe disposal of devices.
Here’s a quick look at how these safeguards come together:
| Safeguard Type | Key Focus Areas | Implementation Examples |
|---|---|---|
| Administrative | Policies and workforce roles | Risk assessments, security officer, staff training, backups |
| Technical | Technology-based protections | Access controls, encryption, audit logs, user authentication |
| Physical | Facility and device security | Access controls, workstation locks, visitor management |
Improving Third-Party and Vendor Risk Management
In healthcare, managing third-party risks has become a critical part of cybersecurity efforts. With hospitals relying on an average of over 1,300 vendors, these external relationships can introduce vulnerabilities that jeopardize patient safety and disrupt operations [5].
Common Third-Party and Vendor Risk Problems
The numbers paint a concerning picture: 55% of healthcare organizations reported a data breach stemming from a third party in the past year, and 90% of major breaches in 2022 involved business associates. Each of these breaches came with an average cost of over $10 million [3].
A major challenge lies in fragmented vendor risk processes. Many healthcare organizations lack the resources to properly follow up on security assessments, leading to inconsistent practices. Vendors and healthcare providers often approach assessments differently, relying on outdated, manual methods that leave critical gaps in security [3]. Adding to the strain, IT teams are inundated with lengthy vendor questionnaires, turning what should be a thorough evaluation into a superficial checklist exercise.
Another pressing concern is the risk posed by vendors with network access through VPNs or other remote connections. Even if patient data remains untouched, cyberattacks targeting these service providers can disrupt essential operations, creating widespread consequences [4].
Step-by-Step Vendor Risk Oversight Strategies
To tackle these challenges, healthcare organizations need a proactive and structured approach to vendor oversight. Key strategies include:
- Focusing on critical vendors: Prioritize those whose services directly affect patient care or revenue.
- Embedding cybersecurity into contracts: Clearly define security requirements in contracts and Business Associate Agreements.
- Conducting in-depth due diligence: Use open-ended questions during onboarding to identify hidden risks.
- Using a Plan of Action and Milestones (POA&M): Track and address vendor risks systematically.
- Involving vendors in cybersecurity planning: Include them in incident response, disaster recovery, and continuity strategies.
- Defining clear roles and responsibilities: Ensure both internal teams and vendors are accountable.
- Planning for secure vendor offboarding: Establish procedures for safe data return or destruction and conduct final audits.
These steps help address common weaknesses in vendor management and enhance overall cybersecurity. The American Hospital Association has highlighted the severity of this issue, stating that cyberattacks on third-party providers can have national consequences, sometimes surpassing the impact of direct attacks on hospitals or health systems [5].
To make these strategies more effective, healthcare organizations increasingly turn to specialized tools.
Using Censinet for Vendor Risk Management
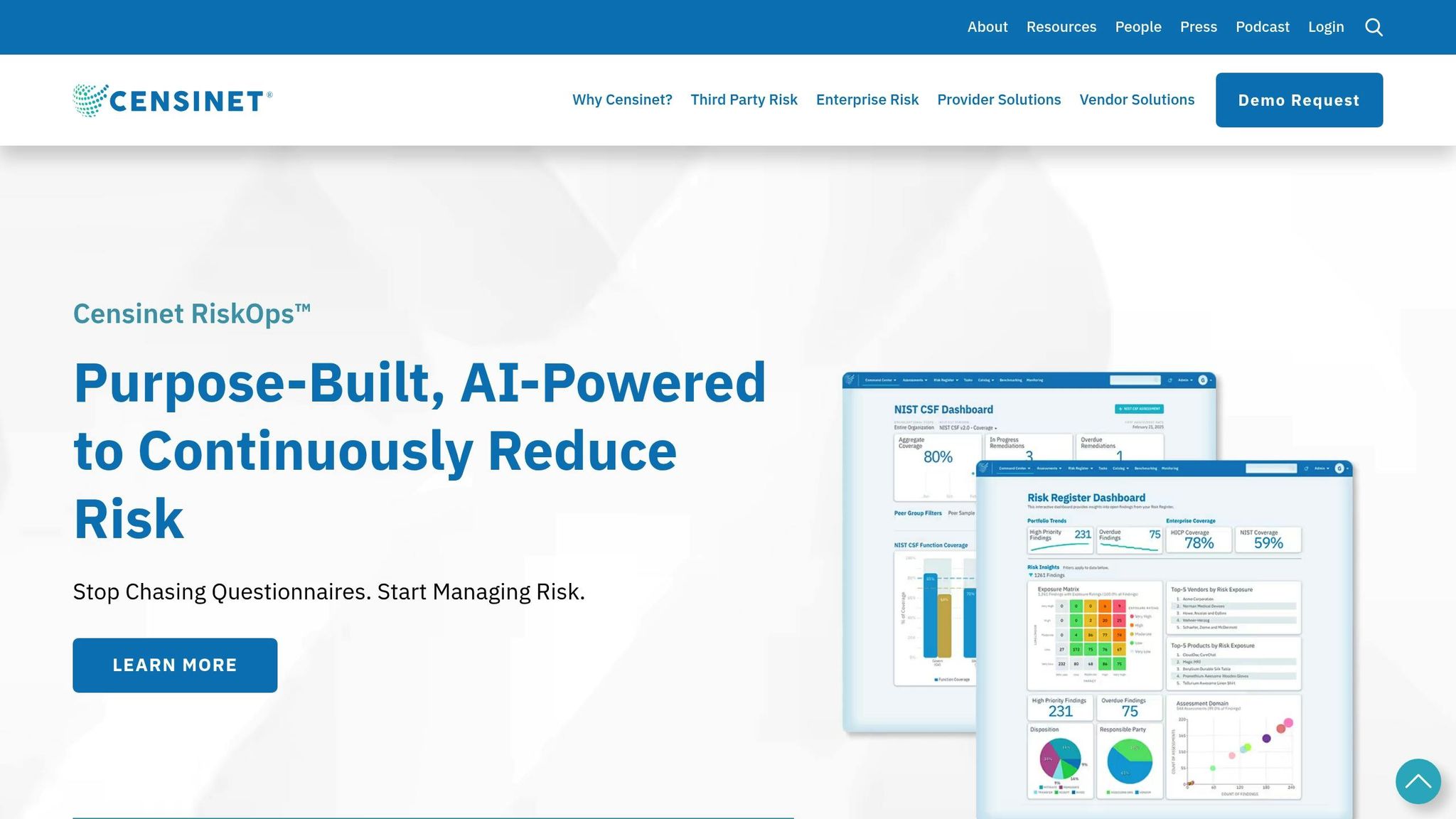
Navigating the complexities of vendor risk management demands tools tailored specifically for healthcare. One such solution is the Censinet RiskOps™ platform, which simplifies the risk assessment process across vendor networks. As Matt Christensen, Sr. Director GRC at Intermountain Health, explains:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [6].
Censinet RiskOps™ addresses risks across the entire ecosystem, including patient data, medical devices, and supply chains [6]. The platform’s efficiency is evident. Terry Grogan, CISO at Tower Health, shares:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [6].
Censinet Connect™ further enhances collaboration between healthcare providers and vendors, enabling secure assessments and ongoing risk monitoring. James Case, VP & CISO at Baptist Health, highlights its impact:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with" [6].
Additionally, Brian Sterud, CIO at Faith Regional Health, emphasizes the importance of benchmarking:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [6].
These tools not only streamline processes but also empower healthcare organizations to strengthen their cybersecurity posture while managing vendor relationships more effectively.
sbb-itb-535baee
Combining Automation and Human Oversight for Better Resilience
Improving cybersecurity in healthcare requires more than just advanced automated tools - it also demands the expertise and judgment of skilled professionals. Striking the right balance between automation and human oversight is critical, especially as data breaches are projected to cost healthcare organizations an average of $9.77 million in 2024 [7].
How Automation Helps Cybersecurity Operations
Cybersecurity in healthcare, much like a robust defense system, works best when it layers automation with human oversight. Automation addresses a key vulnerability in healthcare: human error. For example, 92% of organizations in the UAE reported at least one successful phishing attack in 2023 [7]. Automation can step in to reduce such risks.
Take Role-Based Access Control (RBAC) as an example. By limiting system access to only what’s necessary for specific roles, RBAC helps prevent unauthorized access. Organizations using this approach saw a 35% drop in unauthorized access incidents within six months [7].
Other automated tools, such as 24/7 network monitoring and threat detection, help identify unusual activity and respond faster. Multi-factor authentication (MFA) adds another layer of protection, automatically verifying user identities across multiple channels. Automated patch management ensures systems stay updated against known vulnerabilities without requiring constant manual effort.
Keeping Humans in Control of Key Decisions
While automation reduces errors and streamlines processes, human oversight remains essential for critical decisions, particularly in healthcare. For instance, 83% of U.S. doctors believe AI can benefit healthcare, but 70% are concerned about its role in diagnosing patients [8]. This highlights the need for human experts to validate AI-generated insights with careful judgment and nuanced understanding.
Dr. Eric Topol of the Scripps Translational Science Institute emphasizes this point:
"Humans are important to catch errors or biases in AI results. Working together, human experts and AI can keep trust in medical decisions." [8]
To ensure safety and ethical standards, healthcare organizations should form multidisciplinary AI oversight committees. These teams - comprising clinicians, IT professionals, legal advisors, and ethicists - can evaluate AI tools for accuracy and bias. This is particularly important given that only 44% of hospitals currently assess AI-assisted predictive models for bias [9]. Such oversight ensures seamless integration of cybersecurity measures into clinical workflows while prioritizing patient care.
This collaborative approach also applies to risk management platforms, where automation and human insight intersect.
Using Censinet RiskOps™ as Your Central Risk Management Platform

Censinet RiskOps™ demonstrates how to effectively balance automation with human decision-making in risk management. Its AI-powered tools handle repetitive tasks, such as risk assessments, while leaving critical decisions to human experts through customizable rules and review processes.
The platform’s AI risk scoring and real-time dashboards streamline assessments, cutting completion times to under a day [10]. Meanwhile, Censinet AITM speeds up third-party risk evaluations by enabling vendors to complete security questionnaires in seconds, automatically summarizing their evidence and documentation for review.
Censinet’s real-time AI risk dashboard acts as a centralized hub for managing AI-related policies, risks, and tasks. Think of it as "air traffic control" for AI governance - it ensures that key findings are routed to the appropriate stakeholders for timely review and resolution.
With over 100 provider and payer facilities on its Risk Network and a Digital Risk Catalog™ covering 50,000+ vendors and products [10], Censinet RiskOps™ offers comprehensive visibility while keeping humans in charge of strategic decisions. This approach allows healthcare organizations to scale their risk management efforts efficiently, all while maintaining the critical judgment needed to protect patient safety and comply with regulations. By combining the speed of automation with human expertise, healthcare organizations can build a stronger, more resilient cybersecurity framework.
Measuring Success and Making Continuous Improvements
Effective risk management in cybersecurity isn't a one-and-done effort - it requires ongoing measurement, monitoring, and adjustment. To stay ahead of threats, organizations need to focus on metrics that assess how quickly risks are mitigated, how prepared they are to respond to incidents, and how well they align with frameworks like HIPAA and NIST. Comparing performance with industry peers can also highlight areas needing attention, ensuring security strategies evolve alongside emerging challenges. By using clear metrics, organizations not only track vulnerabilities but also identify actionable steps for improvement. Without this kind of structured measurement, cybersecurity programs can struggle to keep pace with evolving risks.
Key Metrics for Measuring Cybersecurity Maturity
The first step to understanding cybersecurity readiness is choosing the right metrics. One important measure is risk reduction timelines, which track how efficiently vulnerabilities are identified, analyzed, and resolved. Another critical indicator is incident response readiness, which spans detection, containment, and recovery efforts. Organizations that demonstrate high adherence to cybersecurity frameworks and best practices show strong preparedness for threats [11]. Additionally, benchmarking performance against peer institutions can help pinpoint gaps, improve quality, and reduce errors [12].
Setting Up Continuous Monitoring and Benchmarking
Proactive monitoring is essential for identifying vulnerabilities and adapting to new threats. This involves deploying tools that provide real-time updates on network activity, device health, and third-party integrations [13][14]. Automated systems for patch management ensure that software and firmware updates are applied promptly, minimizing exposure to vulnerabilities [14]. Regular audits and security assessments further strengthen defenses by identifying weaknesses, while encouraging employees to report incidents or near-misses creates opportunities for ongoing improvements [1]. These insights feed directly into strategic adjustments, supported by collaborative tools.
Ongoing Improvement with Censinet's Collaborative Tools
Building on continuous monitoring, platforms like Censinet enable organizations to refine their risk management strategies collaboratively. For example, the February 2024 cyberattack on Change Healthcare underscored the urgent need for improved supply chain risk oversight in healthcare, prompting many organizations to reassess their strategies [16].
Ed Gaudet, Censinet's CEO and founder, emphasized the growing urgency:
"With ransomware growing more pervasive every day, and AI adoption outpacing our ability to manage it, healthcare organizations need faster and more effective solutions than ever before to protect care delivery from disruption." [15]
The Healthcare Cybersecurity Benchmarking Study offers practical tools like enterprise assessments, peer comparisons, board-ready reports, and risk mitigation plans [16]. These resources have revealed trends such as slower increases in cyber insurance premiums among organizations using established frameworks, while also highlighting the challenges of early AI adoption. Censinet RiskOps provides a centralized platform for managing AI-related risks, policies, and tasks. Its real-time AI risk dashboard helps leaders track progress on key metrics and address potential issues proactively [15].
John Riggi, National Advisor for Cybersecurity and Risk at the American Hospital Association, summed up the importance of collaboration:
"The Healthcare Cybersecurity Benchmarking Study plays a critical role in uniting the healthcare sector against a growing surge of cyber threats, enabling U.S. hospitals and health systems to better anticipate, withstand, and recover from cyberattacks through collaboration and data-driven insight." [16]
Conclusion: Building Your Complete Risk Management Program
Healthcare organizations are grappling with an alarming rise in ransomware attacks and data breaches, with the average cost of a breach reaching $10.10 million [17][18]. This makes cybersecurity not just a technical issue but a critical part of patient care and the backbone of organizational stability. The need for a comprehensive approach to cybersecurity has never been more urgent.
Instead of relying on small, incremental fixes, healthcare leaders must embrace a transformative approach that fundamentally reshapes how risks are managed.
Key Takeaways
Leading healthcare organizations now understand that cybersecurity is inseparable from patient care and overall resilience. This shift influences everything - how resources are allocated, staff are trained, and security is embedded into daily operations [17].
- Automation and oversight: Striking the right balance between automated systems and human expertise is essential for managing the complexities of healthcare environments.
- Vendor and third-party risks: What was once a compliance checkbox has evolved into a strategic focus, directly tied to patient safety [19][21].
- Continuous measurement: Regularly assessing performance against evolving threats allows organizations to adopt proactive, data-driven strategies that reflect real-world conditions [22].
When these elements come together, they create a risk management program that is far more effective than addressing each component in isolation. With these principles in mind, it's time to focus on actionable steps to drive meaningful change.
Next Steps for Healthcare Organizations
To put these ideas into action, healthcare organizations need to start with a thorough evaluation of their current cybersecurity posture. This involves mapping out the entire threat landscape and understanding how potential incidents could impact both operational goals and patient care [20]. From there, focus on workflows that deliver the most value to the organization while clearly identifying and addressing the associated risks.
Adopting integrated platforms that combine automation with human oversight is crucial. Additionally, fostering collaborative risk networks and benchmarking performance regularly will help organizations stay aligned with industry standards while continuously improving their defenses.
Transforming a risk management program requires significant commitment, resources, and collaboration. However, organizations that take decisive action now will not only navigate today’s cyber threats but also position themselves to thrive in an increasingly digital and complex healthcare environment.
FAQs
How does a healthcare-focused risk management program differ from traditional IT cybersecurity?
Traditional IT cybersecurity typically revolves around technical measures like firewalls, antivirus programs, and regular system updates to guard against general threats. While these defenses work well in many sectors, they often fall short when it comes to the unique demands of healthcare.
In healthcare, risk management requires a more tailored approach. Beyond just technical safeguards, it focuses on protecting sensitive patient data, meeting strict healthcare regulations, and managing risks from third-party vendors. The emphasis is on patient safety, ongoing monitoring, and strategic risk evaluations to address the complex challenges that healthcare organizations encounter daily.
How can healthcare organizations strike the right balance between automation and human expertise to strengthen cybersecurity?
Healthcare organizations can bolster their cybersecurity defenses by blending automation with the insight of human expertise. Automated tools, like AI-powered threat detection systems, excel at spotting and responding to risks swiftly, cutting down on delays and reducing the chance of human error.
That said, human involvement remains crucial for handling more nuanced tasks - like assessing complex risks, making critical decisions, and ensuring cybersecurity measures align with the organization's broader goals and ethical principles. By combining the speed and precision of technology with the reasoning and judgment of skilled professionals, organizations can build a cybersecurity program that tackles both technical vulnerabilities and strategic demands with greater effectiveness.
What are the best strategies for managing third-party and vendor risks in healthcare organizations?
To manage third-party and vendor risks in healthcare effectively, begin with thorough risk assessments to pinpoint potential weak spots. Clearly define contractual requirements that set expectations for security measures and compliance with regulations. It's also essential to regularly monitor vendor security practices to confirm they align with your organization's policies and any updated regulations.
Make ongoing due diligence a priority by evaluating vendor performance and scheduling periodic audits. This approach helps tackle new risks as they arise and bolsters your overall cybersecurity defenses. By staying alert and proactive, healthcare organizations can safeguard sensitive data and maintain trust with both patients and stakeholders.
Related Blog Posts
Key Points:
What is the risk chasm in healthcare, and why is it important to address?
- Definition: The risk chasm represents the gap between traditional, reactive risk management approaches and the proactive, transformational programs required to address modern healthcare challenges.
- Importance: Healthcare organizations face increasing complexity, from cybersecurity threats to regulatory changes. Crossing the risk chasm ensures organizations can align stakeholders, adopt innovative solutions, and build trust across the ecosystem.
Why is crossing the risk chasm important for healthcare organizations?
- Improved Patient Safety: Proactive risk management reduces vulnerabilities that could harm patients.
- Enhanced Compliance: Aligning risk programs with modern standards ensures adherence to regulations like HIPAA and GDPR.
- Operational Resilience: Transformational programs enable organizations to adapt to evolving threats and challenges.
- Innovation Adoption: Crossing the chasm allows organizations to confidently adopt emerging technologies like AI and IoMT.
What are the key challenges in crossing the risk chasm?
- Siloed Systems: Traditional risk management systems often operate in isolation, limiting visibility and collaboration.
- Stakeholder Misalignment: Lack of alignment between departments creates inefficiencies and slows progress.
- Outdated Tools: Legacy systems fail to address modern risks, such as AI-driven cyberattacks or supply chain vulnerabilities.
- Resistance to Change: Cultural resistance within organizations can hinder the adoption of transformational programs.
How can healthcare organizations build a transformational risk program?
- Adopt Network-Based Platforms: Replace siloed systems with integrated platforms that provide real-time insights and collaboration.
- Implement Continuous Monitoring: Use tools that detect risks in real-time, enabling faster responses and proactive mitigation.
- Engage Stakeholders: Align risk management efforts across departments, including IT, compliance, and clinical teams.
- Focus on Proactive Risk Management: Shift from reactive assessments to proactive strategies that anticipate and address risks.
- Leverage AI and Automation: Use AI-powered tools to automate risk assessments, identify vulnerabilities, and enhance decision-making.
What role does stakeholder alignment play in crossing the risk chasm?
- Collaboration: Aligning stakeholders ensures that risk management efforts are coordinated across departments.
- Shared Goals: Stakeholder alignment helps organizations prioritize risks and allocate resources effectively.
- Improved Communication: Open communication fosters trust and transparency, enabling faster decision-making.
What are the benefits of crossing the risk chasm?
- Improved Patient Safety: Reduces risks that could harm patients or disrupt care delivery.
- Enhanced Compliance: Ensures adherence to evolving regulations and standards.
- Reduced Operational Risks: Proactive strategies minimize disruptions and vulnerabilities.
- Innovation Enablement: Organizations can confidently adopt emerging technologies, improving efficiency and outcomes.
- Trust Building: Transformational programs build trust among patients, providers, and regulators.


